Towards the end of January 2022, the Office of Management and Budget (OMB) released its memorandum on moving government agencies to a zero-trust model. Enterprises that align themselves to industries regulated by the federal agencies can take a cue from it to improve their security posture. The memo considers the recent ransomware attacks on various… Continue reading Cues from OMB Zero Trust Architecture memo
Category: Network Security
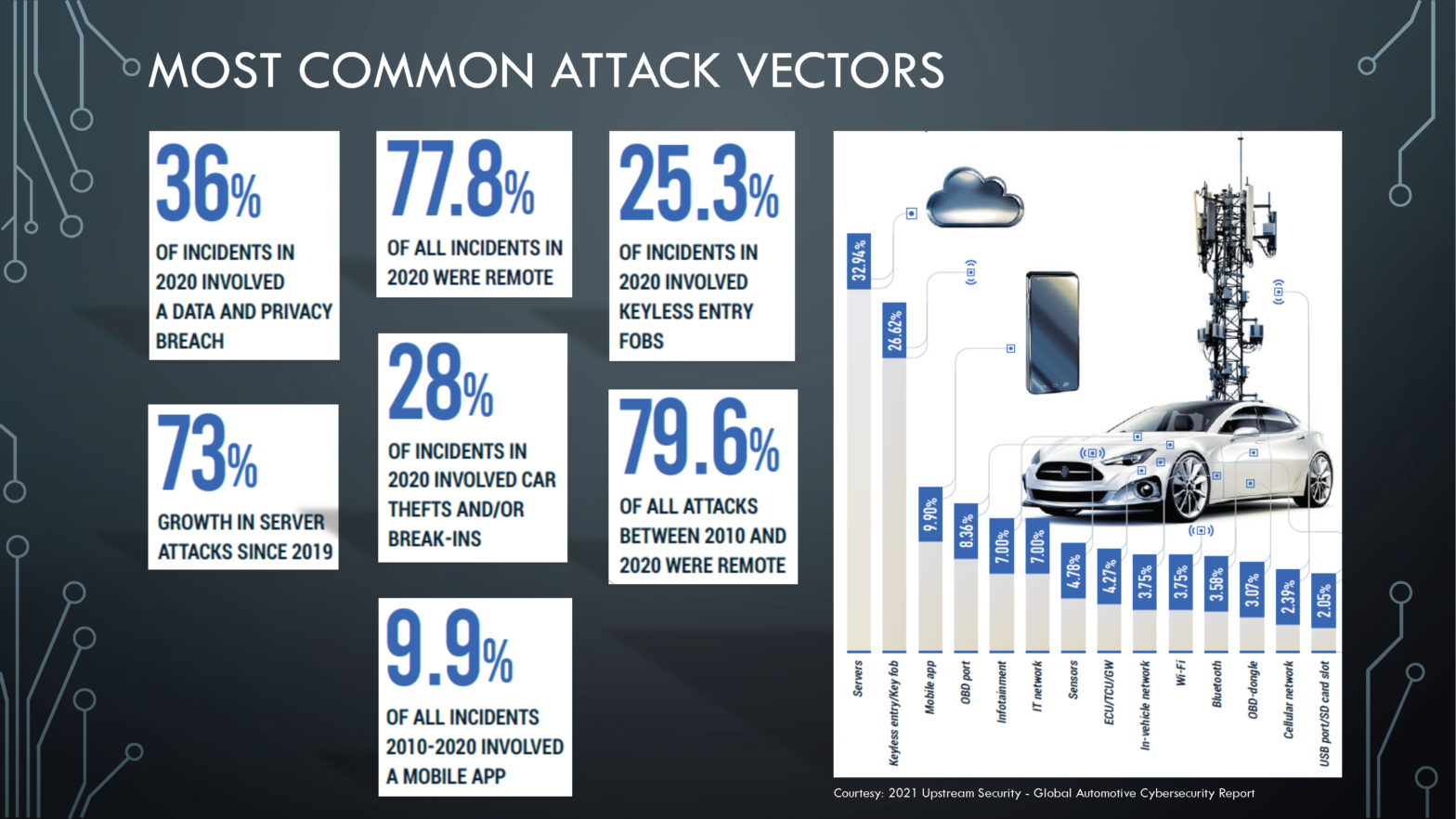
Machine Learning, Society and Cybersecurity
Machine Learning (ML) appears to have made great strides in many areas, including machine translation, autonomous vehicle control, image classification, enabling games on Xbox, PlayStation, Nintendo, and Steam. This has made Artificial Intelligence popular and securing the information in it is challenging. Let’s take a look at an industry that many of us use. We… Continue reading Machine Learning, Society and Cybersecurity
MX Records on Amazon Lightsail
Are you considering moving your Name Server to Amazon Lightsail? You may end up looking for what that “subdomain” means for the MX records. As someone who volunteers for non-profits, I have the opportunity to try out Gmail from G-Suite. As of today (August 25, 2018), Google is yet to provide documentation for Amazon Lightsail… Continue reading MX Records on Amazon Lightsail
Network in Small Businesses
Small cloud businesses are startup companies that rely on Infrastructure-as-a-Service (IaaS) providers for hosting their cloud applications. They could be Software-as-a-Service (SaaS) or Platform-as-a-Service (PaaS) providers for their customers. While relying on the network controls of the IaaS for their applications, small cloud businesses must maintain their own network for business operations and software development.… Continue reading Network in Small Businesses
Hardware or Host Based Firewalls
Do organizations need hardware firewalls when the network already has host-based software firewalls? Wouldn’t it add cost and complexity to networks? Wouldnt system protected by host-based software firewalls just as secure as having a hardware firewall if they are implemented appropriately? “Firewalls actually come in two distinct flavors: software applications that run in the background… Continue reading Hardware or Host Based Firewalls