Small cloud businesses are startup companies that rely on Infrastructure-as-a-Service (IaaS) providers for hosting their cloud applications. They could be Software-as-a-Service (SaaS) or Platform-as-a-Service (PaaS) providers for their customers. While relying on the network controls of the IaaS for their applications, small cloud businesses must maintain their own network for business operations and software development. This paper discusses:
- Common types of networks such as operations networks, software development networks, and production networks found in small cloud businesses at the logical and physical architecture levels.
- Shortcomings in applying defense in-depth security controls in such networks.
- The network security controls required to meet minimum requirements of the industry or community they support.
- The operating systems and how they should be managed and monitored.
- Selected recommendations on how to apply defense in depth beyond the minimum requirements demanded by the industry or government regulations.
Common Networks
Startup companies such as Vapor IO, Hyper-Securing Servers, and Cognitive Scale are examples of small cloud businesses (SCB). (Tsildulko, 2015) They run their business in the cloud. Some of them don’t have a physical office. They are usually PaaS or SaaS providers who are tenants of an IaaS provider. The need for upfront procuring of hardware and software is not required to start a cloud computing business. With the infrastructure already virtualized and available in the cloud, small cloud businesses need to focus on their core service offering. Most of the time, the only asset that the business has is a few laptops. Everything else is in the cloud.
There are three types of network commonly found in small cloud businesses – operations, software development environment, and production as illustrated in Figure 1.
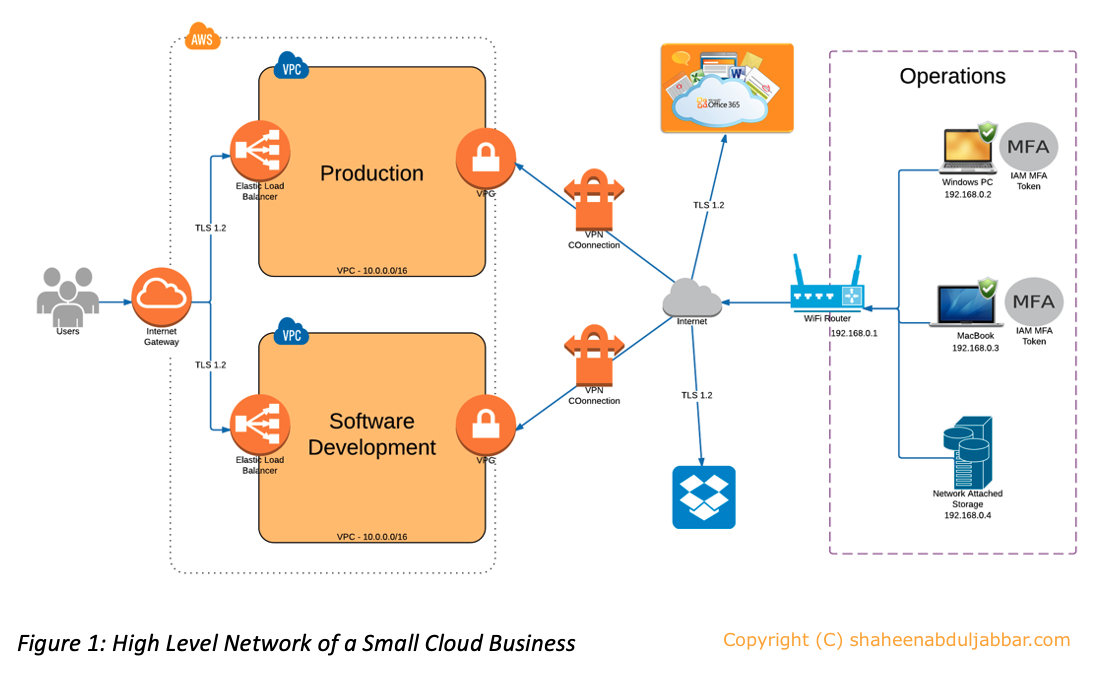
Operations Network
The operations network is where most of the tools used for business functions such as strategic planning, talent planning, expense and capital budgeting, performance management, product planning, and cost accounting resides.
Secured Wi-Fi Network
Very few small cloud businesses have enterprise-level network infrastructure. Often employees sit in an open area with their MacBook or Windows laptop connected to a WPA2 secured Wi-Fi over AES encryption. (Spector, 2011). These routers are hardened with non-generic Admin username and password, rotating non-broadcasted service set identifier (SSID), and the built-in firewall that supports stateful packet inspection (SPI) or network address translation (NAT) enabled. (Griffith, 2016) The protection from these firewalls are minimum and are not enterprise-grade level. Their effectiveness is completely gone when employees connect to the internet from home or other public internet hotspots outside their work location.
MacBook and Windows Laptops
Laptops used in this network either runs on Apple iOS or Microsoft Windows operating systems. The operating systems are patched as and when there is an update available. The user of the laptop is notified by the OS whenever a patch or update is available. However, the laptops are not hardened as in an enterprise. Personnel have administrator privileges and can install any software they wish to. Employees who are software developers may have software development tools such as Java and .Net along with an integrated development environment (IDE) that support such tools. These laptops are protected using security tools such as Norton Security that comes bundled with anti-virus software and firewall. The firewall features include application blocking, connection blocking, and vulnerability protection with location awareness and community-based security intelligence from the security provider. (Symantec Corporation, 2016)
Network Attached Storage (NAS)
NAS is used to store data or files that the business requires offline. The NAS is connected either using a category 5 cable or using Wi-Fi to the Wi-Fi router depending on the NAS capability.
Office Tools
Since Office 365 is available as a cloud service and as an installed application on laptops, it is used as the preferred office tool in small cloud businesses. (Microsoft, 2016) They also use file-sharing services such as OneDrive and Dropbox for storing files and data.
Software Development Network
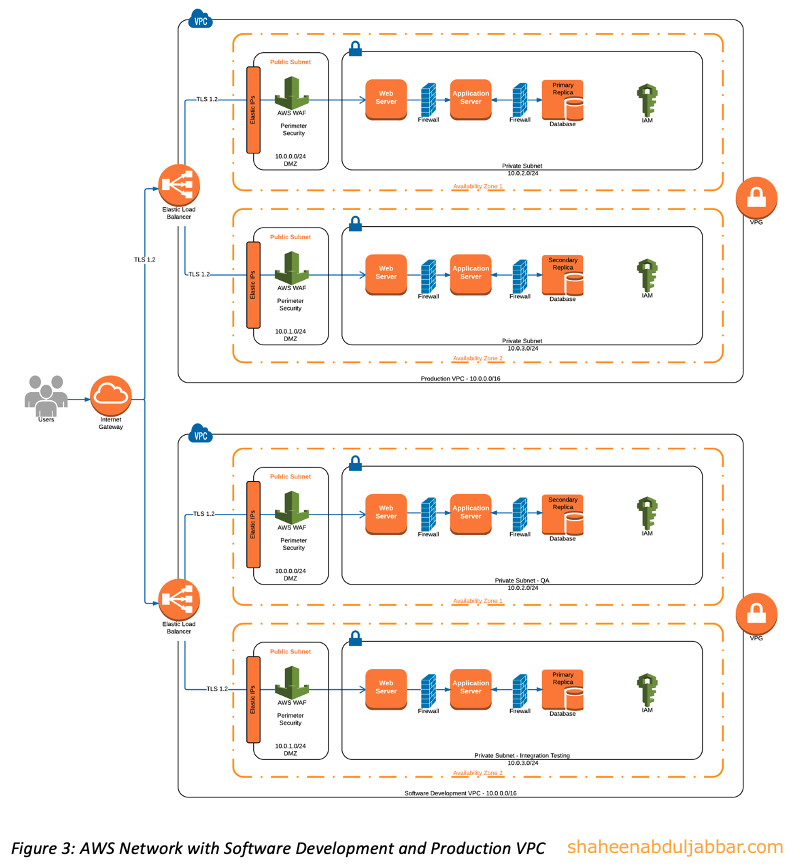
The software development environment is a mix of operations network and the software development VPC (virtual private cloud) network in the cloud. Once the code is written and unit tested within the laptop, it is checked-in to a repository in the cloud service provider to be compiled and executed. It is first tested in the Integration Testing environment and later in the QA environment. These two environments are separate networks within the same VPC. The software development VPC network is separate from the Production VPC network as shown in Figure 2. All change management functions are performed using tools such as Confluence and Jira available in the cloud. (Atlassian, 2016) A static application security testing (SAST) on the code is performed either in the same VPC or at a cloud supply chain provider such as Veracode. (Veracode, 2016) The code is promoted for integration testing only if the results from SAST are satisfactory. Once the integration testing is successful, the code is promoted to Quality Assurance (QA) environment for testing the quality of the code as well as to perform dynamic application security testing (DAST). A provider such as Tinfoil Security (Tinfoil Security, 2016) is leveraged for DAST. (Architect, 2016)
Each cloud instance has a web application firewall (WAF) to protect from malicious traffic from the internet. The data in transit up to the WAF is protected by TLS 1.2. All-access to the VPC requires multi-factor authentication (MFA) token and is through a VPN using a Virtual Private Gateway (VPG). (Amazon Web Services, 2016) The MFA is configured at IAM (Identity & Access Management) service at the cloud instance. The IAM is also leveraged for the logical firewall rules between the web server, application server, and the database using an access control list (ACL) called IAM policies. The IAM policies, adding to defense in depth, serves as a firewall rule except for the fact that these are enforced at the application level and not at the network level. (Amazon Web Services, 2016)
Production Network
This is the environment where the core business function is hosted along with production data to support the function. Production could also be a place where PaaS providers host applications customized for their customers. The setup of the production environment is very similar to a software development environment with actual data and without code repository, change management, and testing tools.
Logical and Physical Architecture
Figures 1 and 2 above illustrates the logical architecture of a small cloud business that describes the network and the networks it connects to. A logical architecture should consider future growth and expansion of the network.
The physical architecture refers to the actual layout of the physical part of the network. It is the actual floor diagram that includes the cables, switches, workstations, etc. (Partsenidis, 2016) In a small cloud business, a physical architecture is almost similar to Figure 1 where the only physical assets that they control are the laptops, Wi-Fi router, and the NAS.
Shortcomings
Operation Network
The operations network in a small cloud business lacks a standard set of operating systems for laptops. Personnel can choose to install what they want. There is no standard process to harden the OS. Developers can download and install any software they want. There is no standard anti-virus (AV) software or host-based firewall. Similarly, there is no standard software development tools. An enterprise-grade operations network with a DMZ is missing. Specific access controls restrictions are required on the files that are stored in NAS. IDS/IPS is rarely considered by small cloud businesses due to the cost of its implementation.
Software Development Network
This network lacks proper access controls to the code repository. There is no segregation of duties in the change management process. Since there is no physical firewall in the cloud, small cloud business has to rely on logical access rules (e.g. IAM policies as in Amazon AWS terms). The change management process that they follow does not include review and approval of logical access rules. Unlike medium and large enterprises, they do not maintain an inventory of all software components used and does not enforce strict use of MFA.
Production Network
Logs of all cloud API calls are missing in the production network. There is always a possibility of a single point of failure if only a single region is used for production. PaaS providers support high availability with redundant regions only when its customer demands it. Multi-tenant customers’ data could be sitting in the same database and sometimes in a jurisdiction outside that of the customers’. MFA is rarely enforced to access sensitive data. There is minimum access restriction to customer data by software developers in production. Sensitive data is in clear beyond the web server. Such data is not encrypted at the data or field level.
Minimum Security Requirements
International laws and legal bodies such as the Privacy Act of 1974 and Safe Harbor in the US, Personal Information Protection and Electronic Documents Act (PIPEDA) in Canada, the European Union Directive 95/46/EC on privacy, and the Australian Privacy Act might relate to where the data is stored or transferred, as well as how well the data is protected from a confidentiality aspect. Some of these laws apply to specific markets, such as the Health Insurance Portability and Accountability Act (HIPAA) for the health-care industry.
Small cloud businesses must adopt network security requirements as described in NIST Special Publication 800-41 Revision 1 Guidelines (Scarfone & Hoffman, 2009) on Firewalls and Firewall Policy which covers packet filtering, stateful inspections, application firewalls, application-proxy gateways, dedicated proxy servers, virtual private network, network access control, unified threat management (UTM), web application firewalls, firewalls for virtual infrastructures, host-based firewalls, and personal firewalls, and personal firewall appliances.
Operating Systems
OS in laptops can be managed using a secure configuration management tool that would help to configure and manage user privileges, remove unused user accounts, close unused open network ports, enforce password complexity & policies, remove unwanted services, and patch all known vulnerabilities. (Shackleford, 2012)
In the cloud, the IaaS provider takes care of monitoring and patching cloud OS. The small cloud business must test such patch roll out in a timely manner. All ports except those managed by the IaaS provider must be managed by the small cloud business. They must close unused open ports. It is up to the small cloud business to decide on password complexities and policies, removal of unwanted services, and user account and privilege management.
Recommendations for Improving Security
The following are recommendations for small cloud businesses to improve their security posture and implement layered security:
- They must have a security policy and standard for its network.
- Security must be part of the overall system development lifecycle
- Apply encryption at the data level so that they need not worry about the location of the data and the jurisdiction where it resides. Data could be anywhere in the cloud. The data owner has full control of the data if the owner or the custodian controls the key.
- Ensure all data containers are encrypted to prevent compromise of data in the case of theft of data containers.
- Segment network based on the classification of data that it would contain.
- Deploy IDS/IPS solution to prevent intrusions. Start with network-based IDS and then depending on the criticality of each host, deploy host-based IDS. (Stallings & Brown, 2015)
- All logical firewall rules and identity access management policies must be reviewed for approval before deploying into production.
- Design the network for high availability by having multiple redundant zones in each redundant cloud regions. Small cloud businesses needs to pay only when those zones or regions are used.
- Perform periodic random tests such as chaos monkey on the network to see its resiliency.
Conclusion
Small cloud businesses will be able to offer its customers a stable and secure service while protecting their own data by having a well-designed network with appropriate security controls based on minimum security guidelines set by NIST. Operating systems in the network can be monitored and managed by secure configuration management tools. Small cloud businesses could improve their data and network security by following the above recommendations.
References
- Amazon Web Services. (2016, December 30). Adding a hardware virtual private gateway to your vpc. Retrieved from aws.amazon.com: http://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/VPC_VPN.html
- Amazon Web Services. (2016, December 30). Overview of IAM policies. Retrieved from aws.amazon.com: http://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies.html
- Architect, C. (2016, December 19). Executive Director. (S. Abdul Jabbar, Interviewer)
- Atlassian. (2016, December 30). Using JIRA for change management. Retrieved from confluence.atlassian.com: https://confluence.atlassian.com/jirakb/using-jira-for-change-management-193300032.html
- Griffith, E. (2016, October 14). 12 ways to secure your Wi-Fi network. Retrieved from pcmag.com: http://www.pcmag.com/article2/0,2817,2409751,00.asp
- Microsoft. (2016, December 30). Office 365 business. Retrieved from office.com: https://products.office.com/en-us/business/office-365-business
- Partsenidis, C. (2016, December 30). What is the difference between physical design and logical design of a network? Retrieved from http://searchnetworking.techtarget.com/: http://searchnetworking.techtarget.com/answer/What-is-the-difference-between-physical-design-and-logical-design-of-a-network
- Scarfone, K., & Hoffman, P. (2009, September 1). Guidelines on firewalls and firewall policy. Retrieved from NIST.gov: http://ws680.nist.gov/publication/get_pdf.cfm?pub_id=901083
- Shackleford, D. (2012, August 1). Secure configuration management demystified. Retrieved from sans.org: https://www.sans.org/reading-room/whitepapers/analyst/secure-configuration-management-demystified-35205
- Spector, L. (2011, November 21). How safe is WPA2-secured WiFi? Retrieved from pcworld.com: http://www.pcworld.com/article/243713/how_safe_is_wpa2_secured_wifi_.html
- Stallings, W., & Brown, L. (2015). Computer Security Principles And Practice. Boston: Pearson.
- Symantec Corporation. (2016, December 30). Norton security premium. Retrieved from Norton: https://us.norton.com/norton-security-with-backup
- Tinfoil Security. (2016, December 30). What exactly does Tinfoil do? Retrieved from tinfoilsecurity.com: https://www.tinfoilsecurity.com/tour
Tsildulko, J. (2015, July 20). The 10 coolest cloud startups of 2015 (so far). Retrieved from CRN: http://www.crn.com/slide-shows/cloud/300077491/the-10-coolest-cloud-startups-of-2015-so-far.htm - Veracode. (2016, December 30). Veracode static analysis. Retrieved from veracode.com: https://www.veracode.com/products/binary-static-analysis-sast