The ISRA methodology is used by a system designer, manager, or security analyst to identify security concerns, develop an action plan, analyze costs, and assign responsibilities. The process allows a facilitator to perform a subjective risk assessment on a particular system, application, or other corporate assets. The ISRA involves the system users
from the very beginning by requiring them to voice their concerns and choose effective controls. (Peltier T. R., 2001)
The ISRA should be part of the SDLC feasibility phase and cost–benefit studies of new systems. It can also be used on existing systems before major updates, during periods of change, or as required by management.
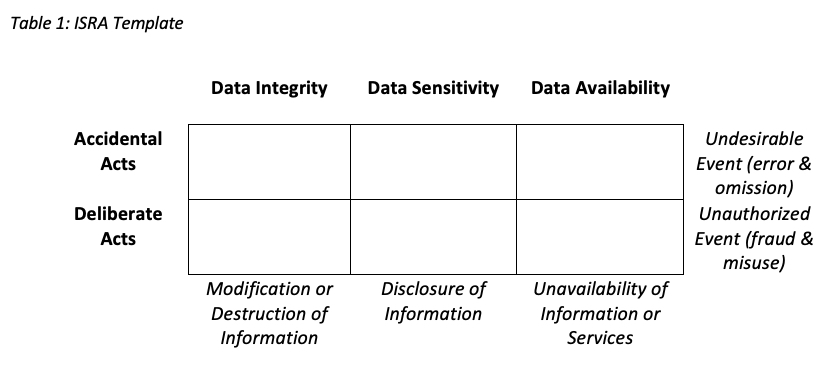
- To perform an ISRA, the facilitator assembles the internal experts of the system or asset being assessed.
- A brainstorming technique is used to prompt the participants to identify risks using a matrix as shown in Table 1
- Each attendee is asked to identify at least three things that could cause his data to be modified or destroyed accidentally, due to the change to the system that is being studied.
- Once the threats are fully identified, the team can select controls (safeguards, standards, rules, etc.) that can best protect against the specific risk.
- When the session is complete, the security staff will create a document detailing the results of the process and presenting security’s conclusions on the existing controls. The risk assessment document will also include an action plan detailing corrective activities to be taken. The action plan will include the time frame to complete the activities and what organization has the responsibility to implement the new or updated controls.
Reference
- Peltier, T. R. (2001). Information Security Risk Analysis. Boca Raton: Auerbach Publications.